-
Notifications
You must be signed in to change notification settings - Fork 91
CVE 2016 5387
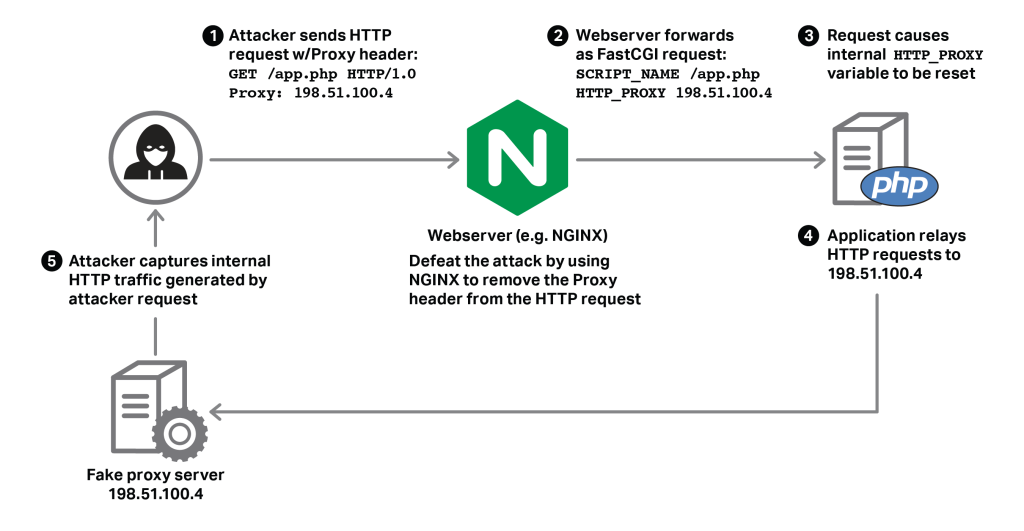
#####The Apache HTTP Server through 2.4.23 follows RFC 3875 section 4.1.18 and therefore does not protect applications from the presence of untrusted client data in the HTTP_PROXY environment variable, which might allow remote attackers to redirect an application's outbound HTTP traffic to an arbitrary proxy server via a crafted Proxy header in an HTTP request, aka an "httpoxy" issue. NOTE: the vendor states "This mitigation has been assigned the identifier CVE-2016-5387"; in other words, this is not a CVE ID for a vulnerability.#####
-
The fix commit for the vulnerability (a git hash)
- 1c660f4f15083b06ce15018d304225c427973c26
-
The commit that introduced the vulnerability (a git hash)
- Due to the nature of the vulnerability (it is a vulnerability in CGI modules that went unmitigated), it would be difficult to say. It is possible that the original introduction of the vulnerability could even be the initial commit. Research has been inconclusive
-
A description of the coding mistake that led to the vulnerability
- A very complete explanation of the bug known as Httpoxy (A play on HTTP_PROXY, the affected environment variable as well as the fact that this bug is considered a "pox" for its ability to hide and randomly pop back up) is available at http://httpoxy.org, as well as the communication from Vend's security team to the Apache Software Foundation to formally disclose the discovery of the bug. The bug originates from CGI putting an HTTP Proxy into an environment variable called HTTP_PROXY. Inherently, this is not a problem, but HTTP_PROXY is a popular name for configuring outgoing proxies. This collision results in the potential for remotely redirecting traffic to an arbitrary proxy server by exploiting this namespace conflict.
- A very complete explanation of the bug known as Httpoxy (A play on HTTP_PROXY, the affected environment variable as well as the fact that this bug is considered a "pox" for its ability to hide and randomly pop back up) is available at http://httpoxy.org, as well as the communication from Vend's security team to the Apache Software Foundation to formally disclose the discovery of the bug. The bug originates from CGI putting an HTTP Proxy into an environment variable called HTTP_PROXY. Inherently, this is not a problem, but HTTP_PROXY is a popular name for configuring outgoing proxies. This collision results in the potential for remotely redirecting traffic to an arbitrary proxy server by exploiting this namespace conflict.
-
Who found it?
- Dominic Scheirlinck- leader of the httpoxy disclosure team
- Scott Geary of Vend
- Stefan Fritsch communicated in the Apache mailing list about it in February 2015
- This vulnerability has, in varying forms, been present since 2001
-
Who fixed it? (Try to get some information on people beyond their name and email)
- The patch was applied over the course of two Github commits by William Rowe
-
Is this code tested by automated tests?
- unsure, likely not. Regardless this would likely not be found by automated testing
-
Was it the same people who found it the ones who fixed it?
- No
-
Read the discussions about the code between introduction and fix. What are the discussions like? Are people discussion requirements, design, security, compatibility, etc? The more you can tie their discussion into the software development process the better. And, again, give me dates and links to actual mailing list discussions. Are there any other linguistic features you notice about these discussions? (e.g. are people angry or polite? terse, or ranty? is there some jargon you notice?)
- There was a very in-depth discussion revolving around fixing the vulnerable file, util_script.c that took place in early to mid July 2016. Although the github commit was significantly later, it would appear that local repositories already contained drafts of fixes for this vulnerability, as they are actively discussing it both before and after its application. There was an extended discussion about how to word the messages- specifically regarding timezones, which appeared to have been affected by the bug fix.
-
Was there a bounty awarded?
- No
-
Any evidence of exploit? Was there a metasploit module made for it, or another exploit related to this (https://www.metasploit.com/).
- It is very likely that this was exploited. There are 9 results on metasploit for this CVE, though none contain exploit modules. Broadening the search to all httpoxy incidents results in 40 vulnerabilities but still no exploit modules. That said there is copious documentation of the threat this vulnerability poses and various mitigations, so despite a complete lack of tangible evidence, minor exploits were most likely commonplace.
-
Any mention of how it was found? Fuzzer? Manual?
- No mention, probably manual
-
Any other significant project-level development events happen during this time? (e.g. dump a related dependency, or change the design in some way)
- There were no major developments happening at this time. Indeed the mailing list was entirely silent for over a week prior to the discovery of the vulnerability, meaning there was likely not much happening in the system.
-
Any other interesting facts about this vulnerability that you would tell someone. Think of yourself as a journalist who is getting a a story together
- Interestingly, Stefan Fritsch noticed the potential for Apache to be hit by the httpoxy vulnerability in February 2015, over a year before it was reported. Unfortunately neither Yann Ylavic nor Nick Kew who responded at the time had the foresight to see through implementation of a proper fix.