JIM is a modern Identity Management system designed for organisations with non-trivial Identity Management and synchronisation requirements. It's designed to be self-hosted, deployable on container platforms and is suitable for connected, or air-gapped networks. Features include:
- Synchronises objects between systems. Supports Users and Groups by default
- Supports custom object types, i.e. Departments, Qualifications, Courses, Licenses, Roles, Computers, etc.
- Transform data using a wide range of functions
- Extensible with custom functions
- Extensible with custom connectors (fully unit-testable)
- A modern Web Portal and API
- Single Sign-On (SSO) using OpenID Connect
JIM is designed to support the following common Identity, Governance & Administration (IGA) scenarios:
- Automate JML by synchronising users from HR systems to directories, apps and systems
- Keep HR systems up to date by writing I.T related attributes back to HR systems, i.e. email address, telephone numbers, etc.
- Centrally manage user entitlements, i.e. group memberships in directories, apps and systems
- Facilitate domain consolidations, i.e. to prepare for migrating to the cloud, simplification, or for organisational mergers
- Facilitate domain migrations, i.e. divestitures
- Identity fusing - bring together user/entitlement data from various business apps and systems
Why choose JIM?
- It's modern. No legacy hosting requirements or janky old UIs
- Supports SSO to comply with modern security requirements
- Open Source. You can see exactly what it does and help improve it
- Flexible. We're developing it now, so you can suggest your must-have features
- Built by people with decades of experience of integrating IDAM systems into the real world
JIM is a container-based distributed application implementing the metaverse pattern for centralised identity governance.
Components:
- JIM.Web - A website with integrated REST API, built using ASP.NET Blazor Server. The API is available at
/api/with Swagger documentation at/api/swagger. - JIM.Scheduler - A console app, built using .NET
- JIM.Worker - A console app, built using .NET
- JIM.PowerShell - A PowerShell module for scripting and automation
- A database - PostgreSQL
- A database admin website - Adminer
For detailed architecture diagrams (Component level), see the Architecture Diagrams.
- A container host, i.e. Docker
- An OpenID Connect (OIDC) identity provider, i.e. Entra ID, Keycloak, etc.
JIM runs in a Docker stack using containers and can be deployed to on-premises infrastructure or cloud container services. JIM is designed for air-gapped deployments - no internet connection is required.
Database Options:
- Bundled PostgreSQL - A PostgreSQL container is included for simple deployments. Start with
docker compose --profile with-db up -d - External PostgreSQL - Connect to your existing PostgreSQL server by configuring
JIM_DB_HOSTNAMEin.envand runningdocker compose up -d(without the profile)
Each release includes a downloadable bundle containing pre-built Docker images, compose files, the PowerShell module, and documentation. See Release Process for details on air-gapped deployment.
JIM is currently targeting the following means of connecting to systems via it's built-in Connectors. More are anticipated, though people will also be able to develop their own custom Connectors for use with JIM to support bespoke scenarios.
- LDAP (incl. Active Directory, AD-LDS & Samba AD)
- Microsoft SQL Server Database
- PostgreSQL Database
- MySQL Database
- Oracle Database
- CSV/Text files
- PowerShell (Core)
- SCIM 2.0
- Web Services (REST APIs with OAuth2/API key authentication)
JIM uses OpenID Connect (OIDC) for Single Sign-On authentication. It is IdP-agnostic and works with any OIDC-compliant Identity Provider, including Microsoft Entra ID, Okta, Auth0, Keycloak, and AD FS. PKCE is used for enhanced security.
For API access, JIM supports both JWT Bearer tokens and API keys for automation and CI/CD scenarios.
For development setup using GitHub Codespaces or local installation, see the Developer Guide.
For SSO configuration with your Identity Provider, see the SSO Setup Guide.
JIM is approximately 94% complete towards MVP status with core identity synchronisation functionality complete. See MVP Definition for detailed progress tracking.
Connectors (Complete):
- LDAP/Active Directory - Full import and export, schema discovery, LDAPS support with certificate validation, auto-detection of default naming context
- CSV Files - Full import and export, configurable delimiters, timestamped outputs
Import (Complete):
- Full import from all connectors with object creation, update, and deletion detection
- Multi-valued attribute handling and all data types supported
Inbound Synchronisation (Complete):
- Join rules to match Connected System Objects to existing Metaverse Objects
- Projection to create new Metaverse Objects
- Attribute flow rules with multi-valued attribute support
- Metaverse Object lifecycle management with deletion rules and grace periods
Outbound Synchronisation / Export (Complete):
- Pending Export detection when Metaverse Objects change
- Export evaluation and execution via connectors
- Create, update, and delete operations in target systems
- Retry logic with exponential backoff
- Pending Export review UI with server-side sorting, filtering, and pagination
Security (Complete):
- SSO/OIDC authentication for Web UI
- JWT Bearer token authentication for API
- API Key authentication for automation and CI/CD
- Role-based authorisation (basic model)
API (Complete):
- Activity monitoring and run profile execution
- Connected Systems, Sync Rules, and Run Profiles CRUD
- Metaverse Object querying with filtering and pagination
- Data generation for testing
- Certificate management
PowerShell Module (Complete):
- 35 cmdlets covering all major JIM operations
- Connection management with API key support
- Full CRUD for Connected Systems, Sync Rules, Run Profiles
- Metaverse Object querying and inspection
- Run profile execution and activity monitoring
- Data generation for testing scenarios
Web UI (Complete):
- Operations view for manual run profile execution and task monitoring
- Activity history with server-side sorting, filtering, and pagination
- Connected Systems management and connector configuration
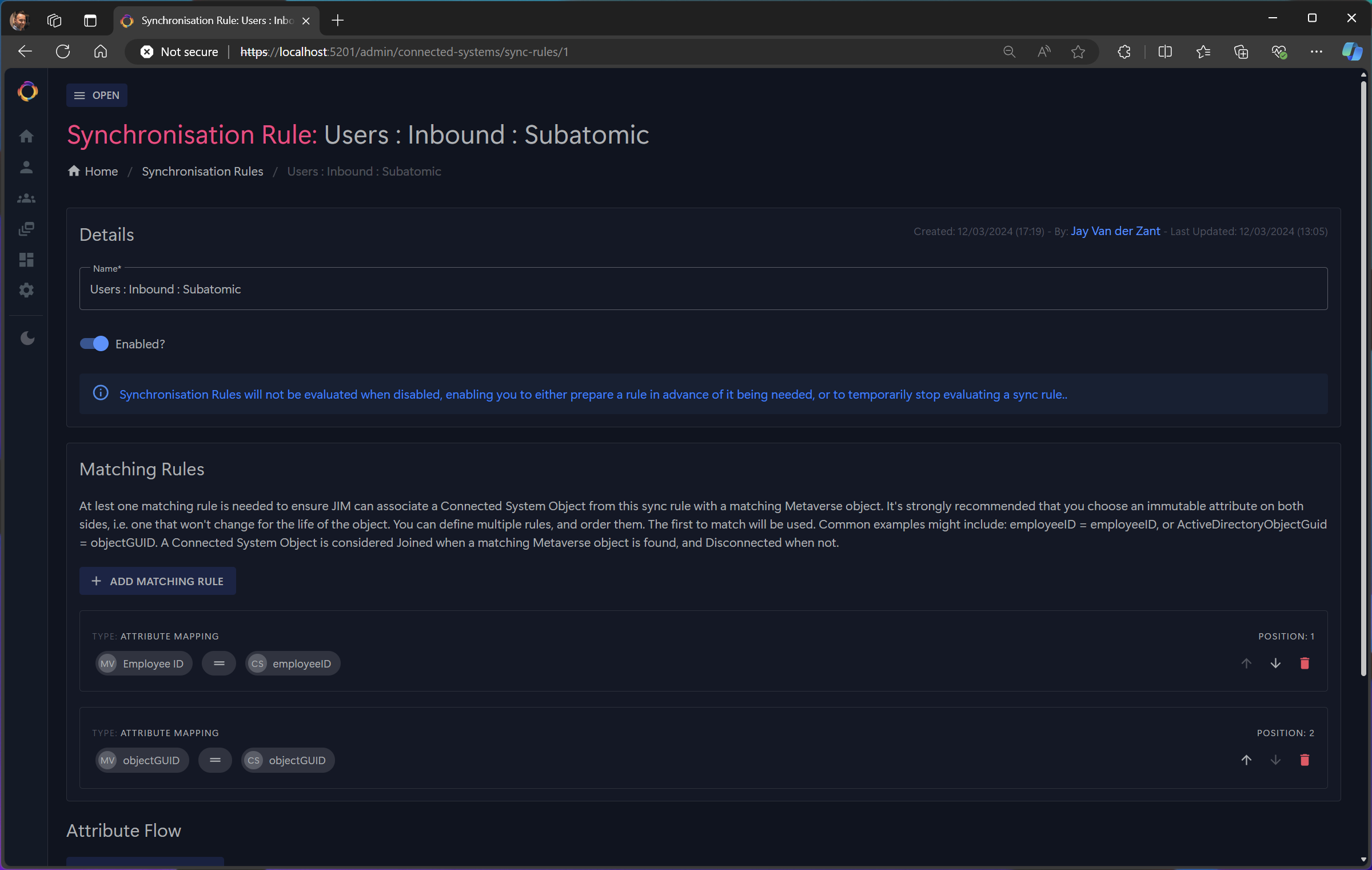
- Sync Rule configuration with attribute flow mapping
- Metaverse Object browsing and inspection
- Pending Export list and detail views
- Certificate management for secure connections
Release & Deployment (Complete):
- Automated release workflow with GitHub Actions
- Docker images published to GitHub Container Registry
- Air-gapped deployment bundles with SHA256 checksums
- PowerShell module auto-published to PSGallery
Testing:
- Unit tests for models, utilities, and API endpoints
- Worker tests for synchronisation logic
- Workflow tests for multi-step sync scenarios (import → sync → export → confirming import)
In Progress:
- Scheduler service for automated run profile execution (critical path for MVP)
- Full RBAC model with additional roles
Note: Integration testing is currently underway. As a pre-MVP release, bugs may exist. Please report any issues on GitHub.
If you don't have any connected systems available, you can use the Example Data feature to populate JIM with sample users and groups for testing.
JIM uses a Source-Available model where it is free to use in non-production scenarios, but requires a commercial license for use in production scenarios. Full details can be found here.
Please go to https://tetron.io/jim for more information.